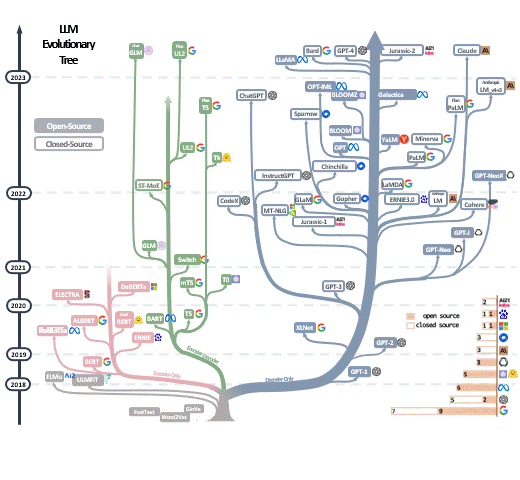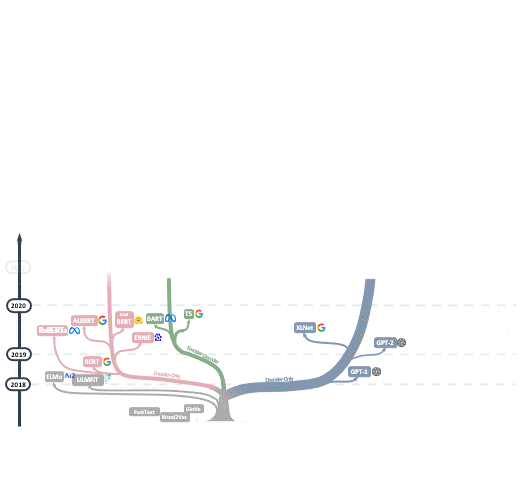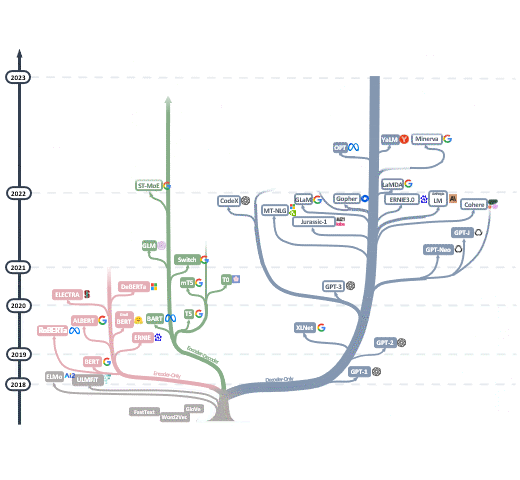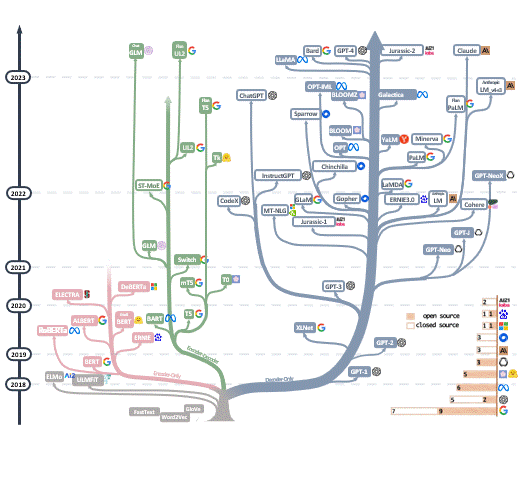
A question driven dive into transformer, mainly to checkpoint my own level of understanding.
Q: What are similarities and differences between autocorrelation used on signals in signal processing and attention used on sequences of word vectors in transformers in deep learning ?
There are some similarities between the attention mechanism and autocorrelation in signal processing, in the sense that both involve computing a similarity measure between a signal and a shifted version of itself.
In autocorrelation, the similarity measure is typically computed as the dot product between the signal and a shifted version of itself. The resulting autocorrelation function can reveal patterns in the signal that are repeated over time, such as periodicity or other types of regularity.
Similarly, in the attention mechanism, the similarity measure between the query and the keys is computed as the dot product, and the resulting attention scores can reveal patterns in the input that are relevant to the query. These patterns can be used to weight the corresponding values when computing the final attention output.
However, there are also some important differences between the two concepts. In signal processing, autocorrelation is used primarily for analyzing signals, while the attention mechanism is used primarily for modeling relationships between elements in a set or sequence. Additionally, the attention mechanism can be more flexible and powerful than autocorrelation, as it can take into account multiple queries and keys simultaneously, and can be applied to a wide range of tasks in natural language processing, computer vision, and other domains.
Q: How are the Q, K, V matrices derived from the input X ? can you confirm that these are functions of X ?
A: The transformer architecture utilizes matrices Q, K, and V which are derived from the input X. The Q, K, and V matrices in the transformer are functions of the input X, derived by applying learned projections. The queries Q represent a lower-dimensional embedding of X optimized for attention, while keys K and values V represent transformations of X optimized for similarity matching and information retrieval. By deriving Q, K, V from X, the transformer architecture can relate elements of the input to one another through scalable self-attention.
Q is derived from X by applying a learned projection to X. “Q is a projection of a learned latent array with index dimension N ≪ M, where the latent’s input is X.” So Q = Projection(X).
K and V are derived by applying projections directly to the input X. Therefore, K = Projection(X) and V = Projection(X).
Q: How are the Q and K matrices incrementally adjusted in the forward and backward passes of back propagation, during training
A: During training with backpropagation:
- In the forward pass, the query Q and key K matrices are initialized randomly and then get updated through backpropagation to learn meaningful representations.
- In the backward pass, the gradients from the loss function are propagated back through the network to update the Q and K matrices:
The gradients for Q and K are computed based on the chain rule. The loss L is differentiated w.r.t the attention weights A, which in turn depends on Q and K.
So
- dL/dQ = dL/dA * dA/dQ and
- dL/dK = dL/dA * dA/dK
These gradients are used to update Q and K with optimization techniques like stochastic gradient descent or Adam.
So in the forward pass Q and K are computed, in the backward pass their gradients are computed and they get updated to minimize the loss. This incremental adjustment via backpropagation allows Q and K to learn optimized representations.
Q: in a transformer with Q, K, V matrices where these are projections of the input X, can you confirm that the associated weight matrices for each transform remain fixed for any input X, that is they are a function of the corpus and training and not an individual input X ?
A: The weight matrices used for these projections remain fixed and are not dependent on any individual input X. The weights are learned during pre-training on the corpus and then fixed after training.
Q: In a transformer, Q, K, V matrices are derived from X as Q = XWQ, K = XWK, and V = XWV . what are the exact dimensions of X, WQ, WK, WV here ?
In the context of the Transformer architecture (as introduced in the “Attention Is All You Need” paper by Vaswani et al.), the matrices QQ, KK, and VV are derived from the input XX using weight matrices WQWQ, WKWK, and WVWV, respectively. The exact dimensions of XX, WQWQ, WKWK, and WVWV are determined by the problem setting and the design choices of the transformer model.
However, for clarity, let’s break down the dimensions based on the original Transformer model:
- XX: The dimension of XX is [T,dmodel][T,dmodel], where TT is the sequence length and dmodeldmodel is the dimension of the embeddings (e.g., 512 in the original Transformer model).
- WQWQ, WKWK, WVWV: These weight matrices are used to project XX into the corresponding QQ, KK, and VV spaces. In the original Transformer, the attention heads operate in a reduced-dimensional space of size dkdk. So, the dimensions of these matrices are:
- WQWQ: [dmodel,dk][dmodel,dk]
- WKWK: [dmodel,dk][dmodel,dk]
- WVWV: [dmodel,dv][dmodel,dv]
In the case of multi-head attention, there are hh heads, and dmodel=h×dkdmodel=h×dk. Typically in the original Transformer, dk=dvdk=dv and is often set to 6464. Hence, for 8 heads (h=8h=8), dmodel=512dmodel=512.
So, given the above:
- QQ will have dimensions [T,dk][T,dk].
- KK will have dimensions [T,dk][T,dk].
- VV will have dimensions [T,dv][T,dv].
However, keep in mind that in the multi-head attention setting, these projections happen independently for each head, resulting in multiple QQ, KK, and VV matrices – one set for each head.
To decide on the exact dimensions in a specific scenario, one would need to know the exact design choices or configurations of the transformer in question.
Q: So there is a difference between d_model and d_k. how is d_k chosen in that paper ?
A: Yes, there is a distinction between d_model and d_k in the Transformer architecture. In the original “Attention Is All You Need” paper by Vaswani et al., the multi-head attention mechanism is introduced. Each “head” of this multi-head attention operates in a reduced-dimensional space defined by dkdk for queries and keys, and dvdv for values.
In the original Transformer model:
dmodel=512dmodel=512
dk=dv=64dk=dv=64
The model uses h=8h=8 heads, which means:
dmodel=h×dkdmodel=h×dk
So, 512=8×64512=8×64.
The choice of dk=64dk=64 in the paper is a design decision, and it’s likely the result of experimentation to find a balance between computational efficiency and model performance. By having a smaller dkdk, the dot products in the attention mechanism are computed in a reduced-dimensional space, which is more computationally efficient. By using multiple heads, the model can still capture different types of attention patterns in parallel.
The paper does not go into explicit detail about how they arrived at dk=64dk=64 beyond this design rationale, and the choice could be the result of empirical testing and optimization.
User
Q: How are the multiple different transformer units strung together ? There are multiple Q, K, V matrices in a single neural network as described in the paper, right ?
A: Absolutely. The original “Attention Is All You Need” paper introduced the Transformer model, which consists of multiple layers of transformer units, and each of these units employs the multi-head attention mechanism. I’ll walk you through how these units are strung together and how multiple QQ, KK, VV matrices come into play.
Multi-Head Attention:
Within a single transformer unit (or layer), there's the concept of multi-head attention. This means the attention mechanism is applied multiple times (with different weight matrices) in parallel. For the original Transformer, this number is h=8h=8.
For each head, separate QQ, KK, and VV matrices are computed, resulting in hh sets of QQ, KK, VV matrices. These are then used to compute hh different attention outputs.
These hh attention outputs are concatenated and linearly transformed to produce a single output for that transformer layer.
Stacked Transformer Layers:
The Transformer model consists of several stacked layers of the transformer units. In the original paper, they used 6 layers for both the encoder and the decoder. Each of these layers has its own set of weight matrices for computing QQ, KK, and VV, and hence, its own multi-head attention mechanism.
The output from one layer is used as the input to the next layer, allowing for increasingly abstract representations as you move up the layers.
Encoder-Decoder Structure:
The original Transformer model has an encoder-decoder structure. Each of these consists of multiple transformer layers.
The encoder takes in the source sequence and produces a representation. This representation is then used by the decoder (alongside the target sequence) to produce the final output.
In the decoder, there are actually two attention mechanisms in each layer: one that attends to the decoder's own previous outputs (self-attention, like in the encoder) and another that attends to the encoder's output (cross-attention).
Residual Connections & Feed-Forward Networks:
Besides the attention mechanisms, each transformer layer also contains a position-wise feed-forward network and residual connections. The output from the multi-head attention is passed through this feed-forward network before being sent to the next layer.
Residual connections help in training deep networks by bypassing layers with the identity function. This is a crucial aspect of the Transformer's architecture.
To visualize, imagine the encoder as a vertical stack of blocks (transformer layers) where each block has 8 separate “channels” or “pipes” (multi-head attention) running through it. The same visualization applies to the decoder, but with an added complexity of having two attention mechanisms in each layer.
Yes, due to the multi-head attention and multiple layers, there are indeed multiple QQ, KK, and VV matrices in the Transformer model as described in the paper.
Q: Can you count exactly how many Q,K, V matrices in total are in the above description ? think step by step
A: Certainly! Let’s break it down step by step for both the encoder and the decoder:
Encoder:
Multi-Head Attention within a Single Layer:
Each transformer layer in the encoder has a multi-head attention mechanism with h=8h=8 heads.
Therefore, for each layer, there are:
8 QQ matrices
8 KK matrices
8 VV matrices
Stacked Transformer Layers:
The encoder consists of 6 stacked transformer layers.
For all layers in the encoder:
QQ: 6×8=486×8=48
KK: 6×8=486×8=48
VV: 6×8=486×8=48
Decoder:
Self-Attention within a Single Layer:
Similar to the encoder, each transformer layer in the decoder has a self-attention mechanism with h=8h=8 heads.
For each layer:
8 QQ matrices for self-attention
8 KK matrices for self-attention
8 VV matrices for self-attention
Cross-Attention to Encoder Output within a Single Layer:
Each transformer layer in the decoder also has a cross-attention mechanism that attends to the encoder's output. This also has h=8h=8 heads.
For each layer:
8 QQ matrices for cross-attention (from the decoder)
8 KK matrices for cross-attention (from the encoder)
8 VV matrices for cross-attention (from the encoder)
Stacked Transformer Layers in the Decoder:
The decoder also consists of 6 stacked transformer layers.
For all layers in the decoder (considering both self-attention and cross-attention):
QQ: 6×8+6×8=966×8+6×8=96 (48 from self-attention and 48 from cross-attention)
KK: 6×8+6×8=966×8+6×8=96
VV: 6×8+6×8=966×8+6×8=96
Total Count:
Adding up both the encoder and the decoder:
Total QQ matrices: 48(fromencoder)+96(fromdecoder)=14448(fromencoder)+96(fromdecoder)=144
Total KK matrices: 48+96=14448+96=144
Total VV matrices: 48+96=14448+96=144
So, in total, across the entire Transformer model (encoder and decoder combined) as described in the original paper, there are:
144 QQ matrices
144 KK matrices
144 VV matrices
Q: Why do they use XWQ instead of the more typical linear transform Wq.X ?
A:
The notation “XW^Q” versus “W^QX” is primarily a matter of convention, and the underlying mathematical operation remains the same. Both notations represent matrix multiplication, but the order of the operands is swapped. The choice of one over the other can be influenced by multiple factors, such as:
Data Representation: In some frameworks or notations, data instances are represented as rows in a matrix (often called "batch-first" convention). In others, data instances are columns (often called "sequence-first" or "time-first" convention). The choice of convention can dictate the order of the matrix multiplication to ensure the dimensions align correctly.
Historical and Cultural Preferences: Some fields or communities have preferred conventions based on historical precedent, educational materials, or influential publications.
Computational Efficiency: Depending on the data storage, memory access patterns, and the specific operations used, one form might be more efficient than the other. This is more of a concern when optimizing at a low level or for specific hardware.
In the “Attention Is All You Need” paper and many deep learning publications, the “batch-first” convention is used, which means input data X is represented with batches as rows. In this format, XW^Q makes sense because each row (data instance) of X is being linearly transformed by W^Q.
On the other hand, if you’re coming from a background where column vectors represent data instances (e.g., traditional signal processing or control systems), the notation W^QX might feel more natural.
It’s essential to be flexible in understanding both notations and to always check the context in which they’re used.
Q: what do you mean by input data X is represented with batches as rows. is each row an embedding vector representing a word ?
A: Yes, I apologize for not being clear. You’re correct. In the context of the Transformer architecture and many deep learning models, when we talk about data XX, it often refers to a matrix where:
Each row corresponds to an embedding vector of a token (e.g., a word or subword).
The number of rows represents the sequence length (i.e., the number of tokens in a given sequence).
For instance, let’s say you’re processing a sentence with 10 words, and you’re using an embedding dimension of 512. Your input XX for that sentence would be a 10×51210×512 matrix. Here, each of the 10 rows is a 512-dimensional embedding vector corresponding to each of the 10 words.
Now, when we introduce batching into the mix:
A batch consists of multiple such sequences (sentences) processed together for computational efficiency.
If you have a batch of NN sentences, and each sentence (sequence) has been padded or truncated to have a length of TT tokens, your batched input data would be a N×T×512N×T×512 tensor.
However, when dealing with linear transformations in the context of the Transformer’s attention mechanism, we’re often focused on one sequence at a time (or a batch of sequences but processed in parallel), so we can think of XX as a T×512T×512 matrix, with TT being the sequence length and 512 being the embedding dimension.
The notion “XW^Q” then makes sense in this context, as each row (token embedding) in XX is transformed by the matrix WQWQ to produce the query matrix QQ.
Q: Can you give some reference papers for applications of group theory in deep learning
A: Absolutely! Here’s a list of notable papers that touch upon the intersection of group theory and deep learning:
- Equivariant Neural Networks:
- “Group Equivariant Convolutional Networks” by Taco S. Cohen and Max Welling. This paper is foundational for introducing group equivariance into CNNs.
- “Steerable CNNs” by Taco S. Cohen et al. This work dives into orientation and scale-equivariant CNNs using steerable filters.
- Invariant Neural Networks:
- “Deep Sets” by Manzil Zaheer et al. This paper isn’t about group theory per se, but it deals with the idea of permutation invariance in neural networks, which relates to certain group symmetries.
- Transformers and Group Theory:
- While the application of group theory to transformers isn’t as well-established as with CNNs, the AlphaFold 2 paper (as we discussed) can serve as a reference for equivariant attention mechanisms.
- General Understanding and Overview:
- “A General Theory of Equivariant CNNs on Homogeneous Spaces” by Taco S. Cohen et al. provides a broader understanding of the topic.
- Applications in Molecular Biology:
- “Equivariant Networks for Molecular Property Prediction” by Bowen Cui, Ivan Zhang, and Zachary Teed explores the applications of group equivariance in predicting molecular properties.
- For More Advanced Topics and Generalizations:
- “Gauge Equivariant Convolutional Networks and the Icosahedral CNN” by Taco S. Cohen et al. explores more advanced structures and symmetries.
While this list provides a good starting point, it’s essential to note that the intersection of group theory and deep learning is an active research area, with new contributions regularly. Keeping an eye on major AI conferences and journals will reveal the latest advancements in this domain.